Data-Centric Security 2024
In an era where data breaches and cyber threats are increasingly sophisticated, organizations are placing greater emphasis on securing their most valuable asset—data. Data-centric security has emerged as a crucial approach that prioritizes the protection of data itself, rather than solely focusing on the perimeter defenses of networks or systems. This paradigm shift reflects a growing recognition that traditional security measures, such as firewalls and intrusion detection systems, may not be sufficient to safeguard sensitive information. The Data-Centric Security Market Growth illustrates this trend, highlighting the increasing investment in comprehensive data protection solutions.
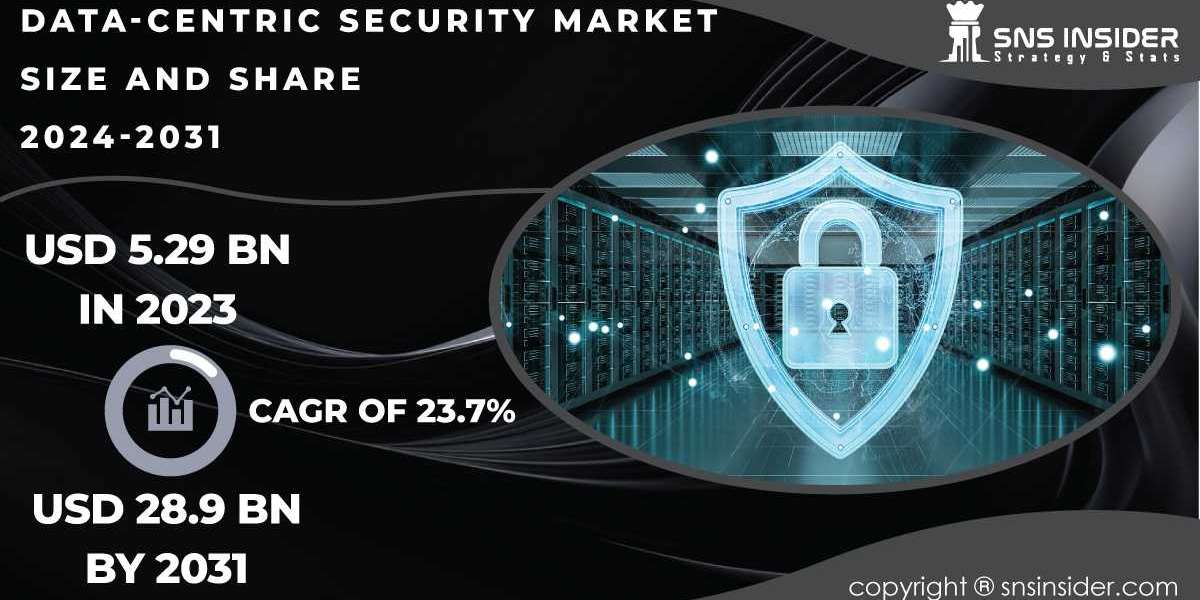
The Data-Centric Security Market was valued at USD 5.29 billion in 2023 and is expected to reach USD 28.9 billion by 2031, growing at a CAGR of 23.7% over the forecast period from 2024 to 2031. This significant growth is driven by the rising number of data breaches, stringent regulatory requirements, and the increasing adoption of cloud services, all of which necessitate a robust security framework focused on data protection.
Understanding Data-Centric Security
Data-centric security refers to a set of strategies and technologies designed to protect data across its lifecycle, regardless of where it is stored or processed. This approach emphasizes the identification and classification of sensitive data, enabling organizations to implement targeted security measures based on the specific risks associated with that data. By focusing on data itself, organizations can enhance their security posture, ensuring that even if a breach occurs, the data remains protected.
Key components of data-centric security include encryption, tokenization, data masking, and access controls. These technologies work together to minimize the risk of unauthorized access and data exposure. For instance, encryption transforms sensitive information into a format that is unreadable without the appropriate decryption key. Tokenization replaces sensitive data with unique identifiers, reducing the risk of exposure while maintaining data usability.
The Importance of Data Classification
A fundamental aspect of data-centric security is data classification, which involves categorizing data based on its sensitivity and the impact of its potential exposure. By classifying data, organizations can prioritize their security efforts, applying the most stringent protections to the most sensitive information. This not only enhances security but also optimizes resource allocation, ensuring that security measures are applied where they are most needed.
Data classification can also help organizations comply with regulatory requirements. Many industries are subject to stringent regulations regarding data protection, such as the General Data Protection Regulation (GDPR) and the Health Insurance Portability and Accountability Act (HIPAA). By effectively classifying and protecting sensitive data, organizations can reduce the risk of regulatory penalties and enhance their overall compliance posture.
Challenges in Implementing Data-Centric Security
Despite its advantages, implementing data-centric security can pose several challenges. One of the primary hurdles is the complexity of data environments. Organizations often manage vast amounts of data across multiple systems, platforms, and locations, making it difficult to achieve a comprehensive understanding of where sensitive data resides. This complexity can lead to gaps in security coverage and increase the risk of data breaches.
Additionally, organizations must contend with the evolving threat landscape. Cybercriminals are continually developing new tactics to exploit vulnerabilities, making it imperative for organizations to remain vigilant and proactive in their security efforts. Continuous monitoring and regular assessments of security measures are essential to stay ahead of potential threats.
The Role of Cloud Computing in Data-Centric Security
The increasing adoption of cloud computing has further underscored the importance of data-centric security. While cloud services offer numerous benefits, including scalability and flexibility, they also introduce unique security challenges. Organizations must ensure that their data remains protected in the cloud, as the shared responsibility model means that both the cloud provider and the organization have roles in securing data.
Data-centric security provides a robust framework for protecting data in cloud environments. By implementing encryption and access controls, organizations can safeguard sensitive information while leveraging the advantages of cloud technology. This approach not only enhances security but also builds trust with customers and stakeholders, demonstrating a commitment to data protection.
Conclusion
In conclusion, data-centric security represents a critical evolution in the field of cybersecurity. By prioritizing the protection of data itself, organizations can enhance their overall security posture and reduce the risk of data breaches. As the Data-Centric Security Market continues to grow, driven by increasing threats and regulatory requirements, organizations must embrace this approach to safeguard their most valuable asset—data. By focusing on data classification, implementing robust security measures, and adapting to the evolving threat landscape, organizations can navigate the complexities of modern data environments and ensure the confidentiality, integrity, and availability of their information.
Contact Us:
Akash Anand – Head of Business Development Strategy
info@snsinsider.com
Phone: +1-415-230-0044 (US) | +91-7798602273 (IND)
About Us
SNS Insider is one of the leading market research and consulting agencies that dominates the market research industry globally. Our company's aim is to give clients the knowledge they require in order to function in changing circumstances. In order to give you current, accurate market data, consumer insights, and opinions so that you can make decisions with confidence, we employ a variety of techniques, including surveys, video talks, and focus groups around the world.
Read Our Other Reports:
Product Life Cycle Management (PLM) Market Report